Unlock Remote IoT Power: Secure SSH, Zero Firewall Hassle!
Ever felt tethered to your desk while your IoT projects hummed away, inaccessible and just out of reach? Imagine a world where geographical boundaries dissolve, and you wield complete control over your Raspberry Pi or other IoT devices from anywhere, anytime. Thats the promise of secure remote IoT access, and its closer than you think.
The ability to manage and monitor IoT devices remotely has rapidly transformed from a luxury to a necessity. Whether you are a hobbyist tinkering with home automation, a developer deploying large-scale sensor networks, or a business ensuring the continuous operation of critical infrastructure, the need for secure and reliable remote access is paramount. The good news is that achieving this level of control no longer requires a degree in cybersecurity or a hefty investment in proprietary software. With the right tools and techniques, securely connecting to your IoT devices is not only possible but surprisingly straightforward.
| Category | Information |
|---|---|
| Topic | Remote IoT Device Management via SSH |
| Key Concepts | Secure Shell (SSH), IoT, Raspberry Pi, Remote Access, Security, Tunneling, OpenSSH, Ngrok, Termius, P2P Connections, VPC, Encryption |
| Benefits |
|
| Tools & Technologies |
|
| Security Measures |
|
| Typical Use Cases |
|
| Reference Website | Raspberry Pi Foundation |
The convergence of the Internet of Things (IoT) and the ever-increasing demand for accessible remote solutions has fueled the development of numerous tools and techniques. This evolution has democratized access, making sophisticated remote management capabilities available even to those with limited technical expertise. Securing these remote connections, however, is non-negotiable. A compromised IoT device can serve as a gateway for malicious actors to infiltrate your network, steal sensitive data, or disrupt critical operations. Therefore, a robust security strategy is essential.
One of the cornerstones of secure remote IoT access is Secure Shell (SSH). SSH is a cryptographic network protocol that enables secure communication between two devices over an unsecured network. It essentially creates an encrypted tunnel, safeguarding data from eavesdropping and tampering. Think of it as a digital fortress, ensuring that only authorized users can access and control your devices. SSH relies on strong encryption algorithms to protect data during transmission, making it an ideal solution for remote management of servers, IoT devices, and other computing systems.
For many, the phrase "remote iot platform ssh raspberry pi download free" can initially seem intimidating. However, setting up SSH on a Raspberry Pi, or any other IoT device, is a relatively straightforward process. A variety of free and open-source tools are available to simplify the configuration and management of SSH connections. One of the primary advantages of SSH is that it eliminates the need to expose your IoT device directly to the public internet. Instead, all communication is routed through an encrypted tunnel, shielding the device from potential threats. This is a critical step in enhancing the overall security of your IoT ecosystem.
Traditionally, establishing remote access required knowing the IoT device's IP address and configuring firewall settings to allow incoming connections. However, modern solutions often circumvent these complexities. One such method involves using encrypted SSH tunnels, where all data is wrapped within a secure channel, eliminating the need to expose the device directly. This significantly reduces the attack surface and simplifies the setup process. Furthermore, utilizing SSH key-based authentication instead of passwords adds an additional layer of security, making it significantly more difficult for unauthorized users to gain access.
- Somali Wasmo Channel Hottest Telegram Groups More
- Uofls Cardbox Free Cloud Storage Amp Collaboration Guide
Remote SSH IoT over the internet is a powerful paradigm for managing smart devices and IoT ecosystems from anywhere in the world. By leveraging free tools like ngrok, Termius, and OpenSSH, you can establish secure and reliable remote access without incurring significant costs. Ngrok, for example, creates secure tunnels to your local machine, allowing you to expose services running on your Raspberry Pi to the internet without the need for port forwarding or complex firewall configurations. Termius provides a user-friendly SSH client with advanced features such as tabbed windows, port forwarding, and snippets for frequently used commands. OpenSSH, a standard SSH implementation, offers robust security features and is widely supported across various operating systems.
The beauty of these solutions lies in their accessibility. You dont need to discover the IoT device IP address or change any firewall settings. The entire process is streamlined, making it accessible even to those without extensive networking knowledge. SSH your IoT device with the system user or SSH key-based secure authentication, using standard client tools such as PuTTY. This combination of ease of use and robust security makes remote SSH a compelling choice for IoT enthusiasts and professionals alike.
However, it is crucial to follow security best practices to protect your devices. Never use default passwords, always enable SSH key-based authentication, and keep your software up-to-date. Regularly audit your system for vulnerabilities and implement intrusion detection systems to identify and respond to potential threats. Security is an ongoing process, not a one-time fix.
Several tools can simplify the process of setting up remote IoT VPC SSH. A VPC, or Virtual Private Cloud, provides a private network within a public cloud provider, such as AWS, where you can securely host your IoT devices and applications. Using a VPC adds an extra layer of isolation and security, protecting your devices from unauthorized access. Setting up SSH access to devices within a VPC typically involves creating a bastion host, which acts as a secure gateway to the private network.
OpenSSH remains a cornerstone of secure remote access. It provides the foundation for establishing encrypted connections and managing authentication. PuTTY, a free SSH client for Windows users, offers a user-friendly interface for connecting to remote devices. FileZilla, a secure file transfer client that supports SSH, allows you to securely transfer files between your local machine and your IoT device.
With the proliferation of IoT devices, managing and monitoring these gadgets from afar has become a necessity for businesses and tech enthusiasts alike. Securing these devices is paramount to prevent unauthorized access and data breaches. Securely connecting remote IoT P2P SSH download on Android ensures that your devices communicate safely over long distances. Peer-to-peer (P2P) SSH for remote access provides a robust solution for accessing IoT devices without exposing them to the public internet. This is a critical step in safeguarding your sensitive data and preventing unauthorized access. P2P connections establish direct communication between devices, bypassing the need for a central server. This can improve performance and reduce latency, particularly for applications that require real-time data transfer.
These tools create a virtual network that enables your devices to communicate securely over the internet as if they were on the same local network. The setup process usually involves installing the software on both the Raspberry Pi and any other devices you want to connect. Configuration typically involves generating SSH keys, configuring firewall rules, and setting up port forwarding (if necessary). Detailed documentation and tutorials are readily available online to guide you through the process.
Securing remote IoT devices using Raspberry Pi is a crucial step in ensuring your projects are safe and reliable. Implementing the right steps will make your projects both secure and reliable. How to securely connect remote IoT P2P SSH Raspberry Pi downloads becomes the central question. The answer lies in a combination of secure configuration, robust authentication, and continuous monitoring.
For SSH tunneling, you can use the following command to create a tunnel:
bashssh -L local_port:remote_host:remote_port user@remote_server
This command forwards traffic from your local machine's `local_port` to the `remote_port` on the `remote_host`, accessible through the `remote_server`. This is an invaluable technique for accessing services running on your IoT device that are not directly exposed to the internet. Remember to replace the placeholders with your actual values.
The adoption of SSH remote IoT device free download is a significant trend. It provides accessible methods for managing IoT devices remotely and has become essential in today's connected world. Remote SSH for IoT devices ensures that projects remain secure while enabling seamless remote access. By using an SSH tunnel, all network traffic is encrypted, ensuring that your data remains confidential and secure. The techniques described here are not just applicable to Raspberry Pi; they can be adapted for various IoT devices and computing systems.
To securely connect your remote IoT devices, you will need a combination of tools and software. These include the SSH client, a P2P solution like RemoteIoT, and your operating system's terminal. Setting up a secure remote IoT environment using VPC SSH on your Raspberry Pi, coupled with straightforward file downloads on Windows 10, is now within your reach, regardless of your experience level.
The convergence of the Internet of Things (IoT) and remote access technologies has revolutionized how we interact with and control devices. Mastering remote IoT VPC SSH on a Raspberry Pi and the accompanying Windows 10 file downloads can significantly enhance your IoT capabilities.
In the context of mastering remote SSH IoT over the internet with AWS, scalability is a crucial factor for organizations looking to manage and control a large number of IoT devices remotely. Designing scalable solutions ensures that the system can handle the increasing number of devices and remote connections without compromising performance or security.
In today's interconnected world, SSH remote IoT Raspberry Pi free download has become a popular topic for tech enthusiasts and professionals alike. Whether you're a hobbyist or a developer, understanding how to download and set up Secure Shell (SSH) on a Raspberry Pi for remote IoT operations can unlock countless possibilities. Setting up remote IoT platform SSH access on a Raspberry Pi involves several steps, including configuring SSH, enabling remote access, and selecting the appropriate platform or software solution. Whether you're using Windows, macOS, or Linux, a variety of free and paid options are available to facilitate this process.
Secure Shell (SSH) is a cryptographic network protocol that provides secure communication over an unsecured network. It encrypts data exchanged between a client and a server, ensuring confidentiality and integrity. The ability to tunnel allows you to interact with services that are not directly exposed to the public internet. This feature is particularly useful for accessing web interfaces, databases, or other services running on your IoT device that are not publicly accessible.
A comprehensive guide, be it for "SSH remote iot raspberry pi download free for windows" or "Iot device remote ssh raspberry pi free download," will typically cover the following key areas: installing and configuring SSH on the Raspberry Pi, setting up SSH key-based authentication, configuring firewall rules, using SSH tunneling for secure access to services, and implementing security best practices. The guide might also include step-by-step instructions on how to use various SSH clients, such as PuTTY and Termius, and how to configure port forwarding for accessing specific services.
Furthermore, a guide on "Introduction to remote iot vpc ssh" would delve into the specifics of setting up a Virtual Private Cloud (VPC) on a cloud platform like AWS and configuring SSH access to devices within the VPC. This would typically involve creating a bastion host, configuring security groups, and setting up SSH key-based authentication.
The phrase "Securely connect remote iot p2p ssh download on android" underscores the importance of mobile access to IoT devices. Many users want to be able to monitor and control their devices from their smartphones or tablets. Setting up SSH access from an Android device typically involves installing an SSH client app, such as Termius or JuiceSSH, and configuring the connection settings. Security considerations are particularly important when accessing IoT devices from mobile devices, as these devices are often more vulnerable to malware and other security threats.
In conclusion, the journey to secure remote IoT access, be it via SSH, P2P connections, or VPCs, is a multifaceted endeavor that requires a solid understanding of networking principles, security best practices, and the available tools and technologies. By following the guidelines outlined above and continuously adapting to the evolving threat landscape, you can confidently manage and monitor your IoT devices from anywhere in the world, secure in the knowledge that your data and systems are protected.
- Iot Device Update Remote Management Best Practices
- Unleash Fun Unblocked Games G For School Home Play

SSH Client SFTP Terminal and Telnet Free download and install on
How to Connect to a Remote Server Over SSH on Windows Linode Docs
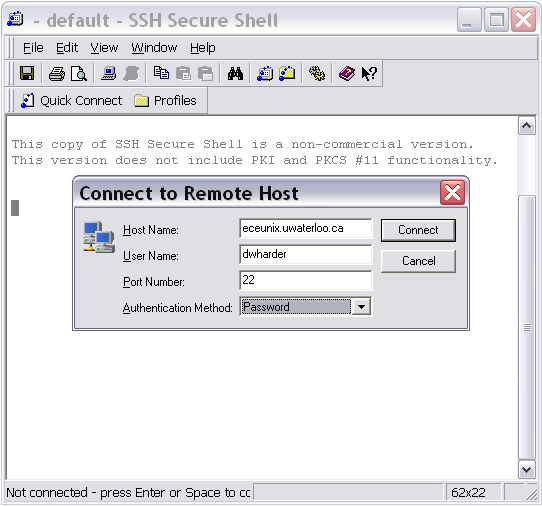
SSH Secure Shell Client MTE 241 University of Waterloo