Remote IoT Behind Firewall On Mac: A Simple Guide + Tips!
Ever feel like your IoT devices are trapped behind a digital fortress? Gaining seamless remote access to your IoT devices, even when they're protected by a firewall, is not just a possibility, it's a necessity for modern efficiency.
In an age where connectivity is king, understanding how to navigate the intricacies of firewalls while managing your IoT infrastructure is paramount. This is especially true for users of Apple's macOS, where a blend of user-friendliness and robust security features presents a unique environment for managing RemoteIoT. The ability to securely connect to and control your IoT devices remotely, regardless of your location or network configuration, can significantly enhance both personal convenience and professional productivity. Let's explore how to make this a reality.
| Category | Information |
|---|---|
| Topic | RemoteIoT Behind Firewall on macOS |
| Key Components | macOS Firewall, RemoteIoT Software, Network Configuration |
| Benefits | Secure Remote Access, Enhanced Productivity, Centralized Control |
| Challenges | Firewall Configuration, Security Risks, Technical Complexity |
| Tools & Technologies | SSH Clients (OpenSSH), VPN Clients (Tunnelblick), Network Monitoring Tools (Wireshark) |
| Further Reading | Apple macOS Security Overview |
The journey to establishing a seamless RemoteIoT setup behind a firewall on your Mac begins with understanding the fundamental role firewalls play. Think of firewall rules as the vigilant gatekeepers of your network's security. When implemented correctly, especially on a macOS system, they are indispensable. They meticulously dictate which types of network traffic are permitted to pass through, effectively shielding your system from unauthorized access and malicious threats.
- Janet Jacksons 2025 Comeback Behind The Scenes Halftime Show
- Find Wasmo Somaliland Telegram Channel Updated
Before diving into the technical configurations, it's crucial to identify the type of firewall you're working with. macOS comes with a built-in firewall, but you might also be dealing with a hardware firewall on your router or a software firewall provided by a third-party security suite. Each type requires a slightly different approach, so understanding your environment is the first key step.
A Mac server offers compelling advantages when managing RemoteIoT behind a firewall. The macOS ecosystem is celebrated for its robust security features and seamless integration with other Apple devices. This makes it an ideal choice for those seeking a reliable and secure setup. Key advantages include:
- Enhanced Security: macOS boasts advanced security protocols that minimize vulnerabilities.
- Seamless Integration: Effortless compatibility with other Apple devices and services simplifies the overall experience.
- User-Friendly Interface: The intuitive macOS interface makes configuration and management more accessible.
- Reliability: macOS is known for its stability, reducing the risk of unexpected downtime.
Now, lets break down the steps necessary to configure RemoteIoT behind a firewall on your Mac:
- Discovering Henry De Niro Early Life Family Legacy
- Itscarlyjanes Leaked Content Whats Trending Now Updated
- Install RemoteIoT Software on Your Mac: The first step is to ensure that the RemoteIoT software is properly installed and configured on your macOS system. This typically involves downloading the software from the vendor's website, following the installation prompts, and configuring the necessary settings.
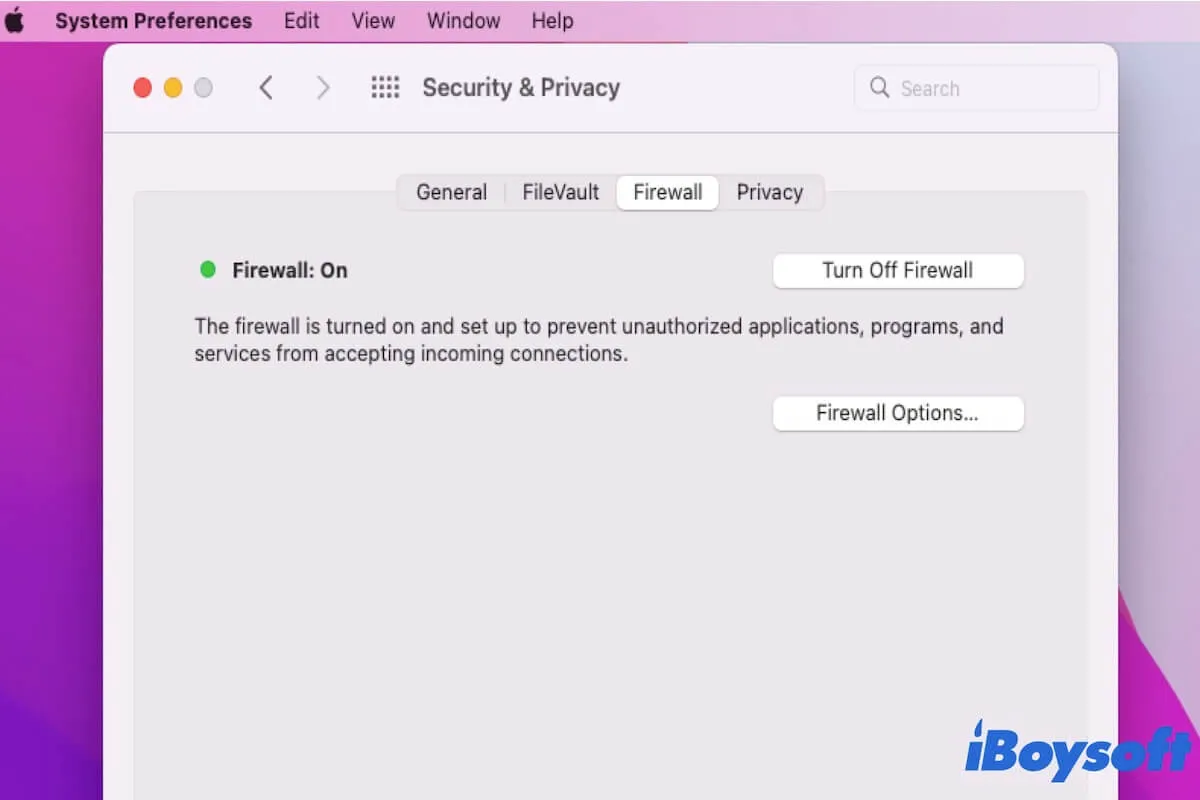
- Configure the Firewall to Allow RemoteIoT Traffic: This is a critical step. You need to tell your firewall to allow incoming and outgoing traffic for the RemoteIoT application. Heres how you can do it using the built-in macOS firewall:
- Go to System Preferences > Security & Privacy.
- Click the Firewall tab.
- Click the lock icon in the bottom left corner and enter your password to make changes.
- Click Firewall Options.
- Click the "+" button to add a new application.
- Navigate to the RemoteIoT application and select it.
- Ensure that "Allow incoming connections" is selected for RemoteIoT.
- Set Up Port Forwarding (If Necessary): If your IoT devices are behind a router that also has a firewall, you may need to set up port forwarding. This involves configuring your router to forward specific ports to the IP address of your Mac server. The specific ports to forward will depend on the RemoteIoT software you are using. Consult the software's documentation for details.
- Test the Connection: Once you've configured the firewall and port forwarding (if necessary), it's time to test the connection. Use a remote device or network to attempt to connect to your RemoteIoT setup. If you encounter any issues, double-check your firewall settings and port forwarding configurations.
Adding RemoteIoT to your firewall is a crucial step to ensure that the software can communicate effectively. Here's a more detailed breakdown of the process:
- Access Firewall Settings:
- Open System Preferences on your Mac.
- Click on "Security & Privacy."
- Select the "Firewall" tab.
- Unlock the Settings:
- Click the lock icon in the bottom left corner of the window.
- Enter your administrator password when prompted. This allows you to make changes to the firewall settings.
- Add RemoteIoT:
- Click the "+" button to add a new application to the list of allowed apps.
- A Finder window will appear, allowing you to navigate to the location of the RemoteIoT application.
- Select the RemoteIoT application.
- Click "Add."
- Verify the Setting:
- Once RemoteIoT is added to the list, ensure that it is set to "Allow incoming connections." This permits the application to receive data from external sources.
Managing RemoteIoT devices behind a firewall using a Mac server might seem daunting at first, but with a systematic approach, it becomes manageable. One key is to utilize the right tools. Some of the best tools for accessing RemoteIoT behind a firewall using your Mac include:
- SSH Clients (e.g., OpenSSH): SSH (Secure Shell) provides a secure, encrypted connection to remote devices. OpenSSH is a free and open-source implementation of SSH.
- VPN Clients (e.g., Tunnelblick): A VPN (Virtual Private Network) creates a secure tunnel between your Mac and the remote network. Tunnelblick is a popular open-source VPN client for macOS.
- Network Monitoring Tools (e.g., Wireshark): Wireshark is a powerful network protocol analyzer that allows you to capture and analyze network traffic. This can be invaluable for troubleshooting network issues.
These tools not only facilitate secure connections but also enable effective monitoring of network traffic, providing insights into potential issues or security threats. Proper configuration and usage of these tools are crucial for a seamless RemoteIoT experience.
Managing RemoteIoT devices behind a firewall on macOS requires a blend of technical knowledge and strategic planning. By following a comprehensive guide, you can establish secure and reliable remote access to your IoT devices. Its essential to regularly review your security settings and stay updated with the latest developments in IoT security.
Connecting to an IoT device behind a firewall involves several methods, each with its own advantages and limitations. Choosing the right method is crucial for ensuring secure and efficient communication. Some common methods include:
- Port Forwarding: Configuring your router to forward specific ports to the IoT device. This allows external traffic to reach the device directly. However, it's important to choose unique and secure port numbers to minimize security risks.
- VPN (Virtual Private Network): Establishing a secure, encrypted connection between your Mac and the network where the IoT device resides. This method provides a high level of security and privacy.
- Reverse SSH Tunneling: Creating an SSH tunnel from the IoT device to an external server. This allows you to connect to the device through the tunnel, bypassing the firewall.
- Cloud-Based Solutions: Using a cloud-based platform to manage and access your IoT devices. These platforms often provide secure and scalable solutions for remote access.
Each method requires a different level of technical expertise and offers varying degrees of security and convenience. Evaluating your specific needs and resources will help you choose the most appropriate method for your RemoteIoT setup.
Firewalls serve as the guardians of network security, but they can also present challenges for remote IoT management. Understanding how to navigate these challenges is crucial for establishing a seamless and secure connection. This article provides a detailed walkthrough on using RemoteIoT behind a firewall on a Mac, from grasping the fundamentals to implementing advanced solutions. The goal is to empower you with the knowledge and tools needed to effectively manage your IoT devices, regardless of the network configuration.
Configuring your router to forward specific ports to the IoT device is a common method for enabling remote access. Heres a breakdown of the process:
- Access Your Routers Configuration Page: This typically involves typing your routers IP address into a web browser (e.g., 192.168.1.1 or 192.168.0.1).
- Log In: Enter your routers username and password. If you havent changed them, check your routers documentation for the default credentials.
- Navigate to Port Forwarding Settings: Look for a section labeled "Port Forwarding," "Virtual Server," or something similar.
- Add a New Port Forwarding Rule:
- Enter a descriptive name for the rule (e.g., "RemoteIoT Access").
- Specify the external port(s) that you want to forward. Choose a port number that is not commonly used to minimize security risks.
- Enter the internal IP address of your Mac server.
- Specify the internal port(s) that the traffic should be forwarded to. This will depend on the RemoteIoT software you are using.
- Select the protocol (TCP or UDP) that the traffic will use.
- Enable the rule.
- Save Your Changes: Be sure to save your changes and restart your router if necessary.
Port forwarding can be a powerful tool, but its important to implement it carefully. Always choose secure port numbers and regularly review your port forwarding rules to ensure that they are still necessary and properly configured.
RemoteIoT is a potent tool that empowers users to securely connect to their IoT devices. Whether you're managing IoT devices remotely or troubleshooting network issues, understanding how to navigate firewalls is crucial. This capability opens up a world of possibilities for both personal and professional use.
As businesses and individuals increasingly rely on IoT devices, comprehending how to configure these tools securely is indispensable. Remote connecting IoT devices behind a firewall on a Mac has gained paramount importance for both personal and professional applications. Whether you are a technology enthusiast or a business professional, mastering the secure remote connection of IoT devices can amplify productivity and convenience.
By adhering to the steps outlined in this guide, you should be able to set up everything without excessive difficulty. Remember, firewalls are in place to protect you; avoid disabling them altogether simply to simplify matters.
Let me explain it in a manner that is both straightforward and actionable. Imagine possessing complete command over your IoT devices, even when they are securely tucked away behind a corporate firewall.
Using RemoteIoT behind a firewall on a Mac can be both a demanding and fulfilling endeavor if executed correctly. It necessitates a combination of technical expertise and meticulous planning.
In today's digital era, grasping how to utilize RemoteIoT behind a firewall using a Mac server is essential for seamless connectivity.
By the conclusion of this article, you will possess a comprehensive understanding of the tools, techniques, and strategies required to effectively use RemoteIoT behind a firewall on a Mac.

How To Use RemoteIoT Behind Firewall Using Mac The Ultimate Guide
How To Use RemoteIoT Behind Firewall Using Mac The Ultimate Guide

How To Use Remote IoT Behind Firewall Mac Without Restrictions A