Easy Remote Access: SSH Ubuntu Server For IoT Devices
Ever found yourself miles away from your devices, needing to tweak a setting or check on their status? Remote access to your IoT devices via SSH on an Ubuntu server isn't just a convenience; it's a necessity for maintaining control and ensuring seamless operation in today's interconnected world. It transforms your ability to manage and interact with your devices from a local inconvenience to a global possibility.
The Internet of Things (IoT) has woven itself into the fabric of our lives, permeating industries from smart homes to industrial automation. As these devices become increasingly integral, the ability to securely access and manage them remotely becomes paramount. A Linux server, particularly one running Ubuntu, provides a robust platform for establishing secure connections with your IoT devices. Secure Shell (SSH) offers a secure method to communicate with these remote devices, guaranteeing data integrity and confidentiality. Setting up a Linux server for remote SSH access unlocks the full potential of your IoT infrastructure, enabling you to monitor, manage, and troubleshoot your devices from anywhere in the world.
| Topic | Information |
|---|---|
| Remote Access via SSH | Enables secure management and control of IoT devices from any location. |
| Ubuntu Server | A popular and reliable Linux distribution widely used for IoT applications. |
| Secure Shell (SSH) | A network protocol providing a secure channel for communication with remote devices, encrypting data to prevent interception and authenticating users for secure access. |
| Key Benefits | Data Integrity, Secure Communication, Remote Management, Operational Efficiency. |
| Reference Website | Ubuntu Server Official Website |
The first crucial step in achieving this remote control is to set up your Linux server for remote SSH access. This involves configuring IP addresses and Domain Name System (DNS) settings so that your server and IoT devices can be identified and reached across the network. This configuration is the foundation upon which secure communication will be built.
- Tom Ackerleys Secret Harry Potter Role Revealed Slytherin Scene Explained
- Taylor Learmont From Hometown Gymnast To Fitness Olympia Star
Setting up SSH on Ubuntu is generally straightforward. The initial task involves installing the OpenSSH server, a widely used and trusted implementation of the SSH protocol. This can be accomplished by opening a terminal and running the command: sudo apt update && sudo apt install openssh-server. This command updates the package lists and then installs the OpenSSH server package, enabling SSH functionality on your Ubuntu server. Once installed, the SSH service should start automatically, allowing you to connect to it remotely.
With the SSH server installed, the next step is to configure it for optimal security. The default SSH configuration often allows for password-based authentication, which can be vulnerable to brute-force attacks. A more secure alternative is to use SSH keys, which provide a cryptographic method of authentication that is much harder to compromise. Generating SSH keys involves using the ssh-keygen command. This command creates a pair of keys: a private key, which you keep secret on your local machine, and a public key, which you copy to the remote server. To enhance security, you can also disable password authentication in the SSH configuration file (/etc/ssh/sshd_config) by setting PasswordAuthentication no. After making this change, remember to restart the SSH service using sudo systemctl restart sshd to apply the new configuration.
Beyond basic configuration, securing your SSH server also involves choosing a strong password for any user accounts that may still use password authentication, changing the default SSH port (22) to a non-standard port, and implementing a firewall to restrict access to the SSH port to only trusted IP addresses. Tools like ufw (Uncomplicated Firewall) can be used to easily manage firewall rules on Ubuntu. For example, you can allow SSH traffic from a specific IP address using the command: sudo ufw allow from 192.168.1.100 to any port 22. These measures significantly reduce the risk of unauthorized access to your server.
- Michael Steeles Msnbc Salary Whats He Earning Now
- Unlock Iot Device Management Free Platforms Remote Access Guide
Once your Linux server is configured, the next step is to set up SSH on your IoT devices. The process is similar to setting up SSH on the server, involving enabling the SSH service, generating keys, and securing the connection. Follow these steps to enable SSH on your IoT device: open a terminal and run sudo apt update && sudo apt install openssh-server. As with the server, consider disabling password authentication and using SSH keys for enhanced security.
A critical aspect of remotely accessing IoT devices is dealing with firewalls and network address translation (NAT). Often, IoT devices are located behind firewalls that prevent direct access from the outside world. SSH tunneling, also known as port forwarding, provides a solution to this problem. SSH tunneling allows you to create a secure channel through the firewall, forwarding traffic from a local port on your server to a remote port on your IoT device. This enables you to access services running on the IoT device as if they were running on your local network. For example, if you have a web server running on your IoT device on port 80, you can forward port 8080 on your server to port 80 on the IoT device using the command: ssh -L 8080:localhost:80 user@iot_device_ip. This creates a tunnel that allows you to access the web server by browsing to localhost:8080 on your server.
Connecting remote IoT devices securely using peer-to-peer (P2P) SSH on an Ubuntu server is essential for safeguarding sensitive data and ensuring seamless communication. This approach is particularly valuable in environments where direct access to IoT devices is restricted by firewalls or NAT. P2P SSH involves establishing a direct connection between your server and the IoT device, bypassing the need for a central relay server. This not only improves security but also reduces latency and increases bandwidth.
One common method to remotely access a Linux server is using Secure Shell (SSH), a network protocol that provides a secure way to communicate with a remote device. SSH encrypts data to prevent interception, authenticates users to ensure secure access, and provides a secure channel for file transfers and remote commands. It is an ideal choice for securing IoT devices in remote locations, especially when dealing with sensitive data or critical infrastructure.
Ubuntu is a popular Linux distribution widely used in IoT applications due to its stability, security, and ease of use. Setting up SSH on Ubuntu is straightforward, but it requires careful attention to detail to ensure that the connection is secure and reliable. This guide will walk you through the necessary steps to establish a secure connection between IoT devices and an Ubuntu server using SSH.
By utilizing a Linux server, you can establish secure connections and ensure seamless communication with your IoT devices. This guide will walk you through the process of setting up a Linux server for remote accessing IoT devices. With Ubuntu, you can easily set up and configure SSH for remote access to your IoT devices, ensuring a secure and efficient environment.
In today's interconnected world, the security of IoT devices cannot be overlooked. As more devices become part of the Internet of Things (IoT), ensuring secure communication is vital to protect sensitive data and maintain operational integrity. Securely connecting remote IoT devices using P2P SSH on Ubuntu is essential for safeguarding sensitive data and ensuring seamless communication. This article will walk you through the process of setting up remote SSH access on Ubuntu, ensuring secure communication, and troubleshooting common issues. By the end of this guide, you'll have a solid understanding of remote IoT web SSH on Ubuntu, enabling you to streamline your IoT projects and maintain secure connections.
With remote access to IoT devices through SSH Ubuntu, you can control your devices from anywhere, anytime. It's like having a superpower for tech enthusiasts. Remote access to IoT devices through SSH isn't just a tech buzzword; remote access through SSH on Ubuntu server allows you to securely connect to your devices, ensuring that no matter where you are, your IoT network remains under your control.
The steps to set up SSH access to an IoT device behind a firewall involves several critical configuration steps. First, make sure the SSH server is running on the IoT device. Let's dive in and unlock the full potential of your Linux device with remote access from anywhere via SSH!
Once you've established a secure SSH connection, you can use it to perform a variety of tasks on your IoT devices. You can remotely execute commands, transfer files, monitor system resources, and troubleshoot issues. For example, you can use the top command to monitor CPU usage and memory consumption, the df -h command to check disk space usage, and the netstat -tulnp command to list listening network ports. These tools provide valuable insights into the health and performance of your IoT devices.
Troubleshooting SSH connection issues can sometimes be challenging. Common problems include incorrect IP addresses, firewall restrictions, and authentication failures. If you're having trouble connecting to your SSH server, first check that the server is running and that the firewall is configured to allow SSH traffic. You can use the systemctl status sshd command to check the status of the SSH service and the ufw status command to check the firewall configuration. If you're using SSH keys for authentication, make sure that the public key is correctly installed on the server and that the permissions on the ~/.ssh directory and ~/.ssh/authorized_keys file are set correctly.
Another common issue is network connectivity. If your IoT device is behind a firewall or NAT, you may need to configure port forwarding to allow SSH traffic to reach the device. You can also use a VPN (Virtual Private Network) to create a secure tunnel between your local network and the network where your IoT device is located. A VPN encrypts all traffic between your device and the VPN server, providing an additional layer of security.
In addition to SSH, there are other tools and technologies that can enhance the security and management of your IoT devices. One such tool is fail2ban, a software package that automatically bans IP addresses that exhibit malicious behavior, such as repeated failed login attempts. Fail2ban monitors system logs for suspicious activity and automatically updates firewall rules to block offending IP addresses. This can significantly reduce the risk of brute-force attacks on your SSH server.
Another useful technology is intrusion detection and prevention systems (IDS/IPS), which monitor network traffic for malicious activity and take action to prevent or mitigate attacks. IDS/IPS systems can detect a wide range of threats, including port scans, denial-of-service attacks, and malware infections. These systems provide an additional layer of security that can help protect your IoT devices from sophisticated attacks.
Regularly updating your software is crucial for maintaining the security of your IoT devices. Software updates often include security patches that address known vulnerabilities. By keeping your operating system and applications up to date, you can reduce the risk of exploitation by attackers. Ubuntu provides automatic updates, which can be configured to install security patches automatically.
Monitoring the security of your IoT devices is an ongoing process. Regularly review system logs for suspicious activity, monitor network traffic for unusual patterns, and perform vulnerability scans to identify potential weaknesses. There are many tools available for monitoring security, including log analysis tools, network traffic analyzers, and vulnerability scanners. By proactively monitoring your devices, you can detect and respond to security incidents before they cause significant damage.
Implementing a strong security policy is essential for protecting your IoT devices. The policy should define the security requirements for your devices, including password complexity requirements, access control policies, and incident response procedures. It should also outline the responsibilities of users and administrators in maintaining the security of the devices. By establishing a clear security policy, you can create a culture of security awareness and ensure that everyone understands their role in protecting your IoT infrastructure.
In conclusion, setting up secure remote access to your IoT devices using SSH on Ubuntu is a critical step in ensuring the security and manageability of your IoT infrastructure. By following the steps outlined in this guide, you can establish a secure connection between your devices and your server, allowing you to monitor, manage, and troubleshoot your devices from anywhere in the world. Remember to prioritize security by using SSH keys, changing the default SSH port, implementing a firewall, and regularly updating your software. With these measures in place, you can confidently deploy and manage your IoT devices, knowing that they are protected from unauthorized access and malicious attacks.
Furthermore, consider the physical security of your IoT devices. Securing the physical environment can prevent unauthorized access and tampering. Implement measures such as locked enclosures, surveillance cameras, and alarm systems to protect your devices from physical threats.
Educating users about security best practices is also crucial. Users should be trained to recognize phishing attacks, avoid clicking on suspicious links, and protect their passwords. Regular security awareness training can help users understand the risks and take appropriate measures to protect themselves and your IoT infrastructure.
Finally, develop an incident response plan to prepare for potential security breaches. The plan should outline the steps to take in the event of a security incident, including identifying the incident, containing the damage, eradicating the threat, and recovering from the incident. Regular testing of the incident response plan can help ensure that it is effective and that everyone knows their role in the event of a security breach.
By combining technical security measures with physical security and user education, you can create a comprehensive security posture that protects your IoT devices from a wide range of threats. This will enable you to confidently deploy and manage your IoT infrastructure, knowing that it is secure and reliable.
- Sione Papalii Fitisemanu A Legacy Of Family Rugby Star
- Lacykim Onlyfans Leaks Nudes Videos 2024 Update Free

ASUS IoT and Canonical partner on Ubuntu Certification for IoT
IIOT Remote access platform for IoT devices High Peak Software
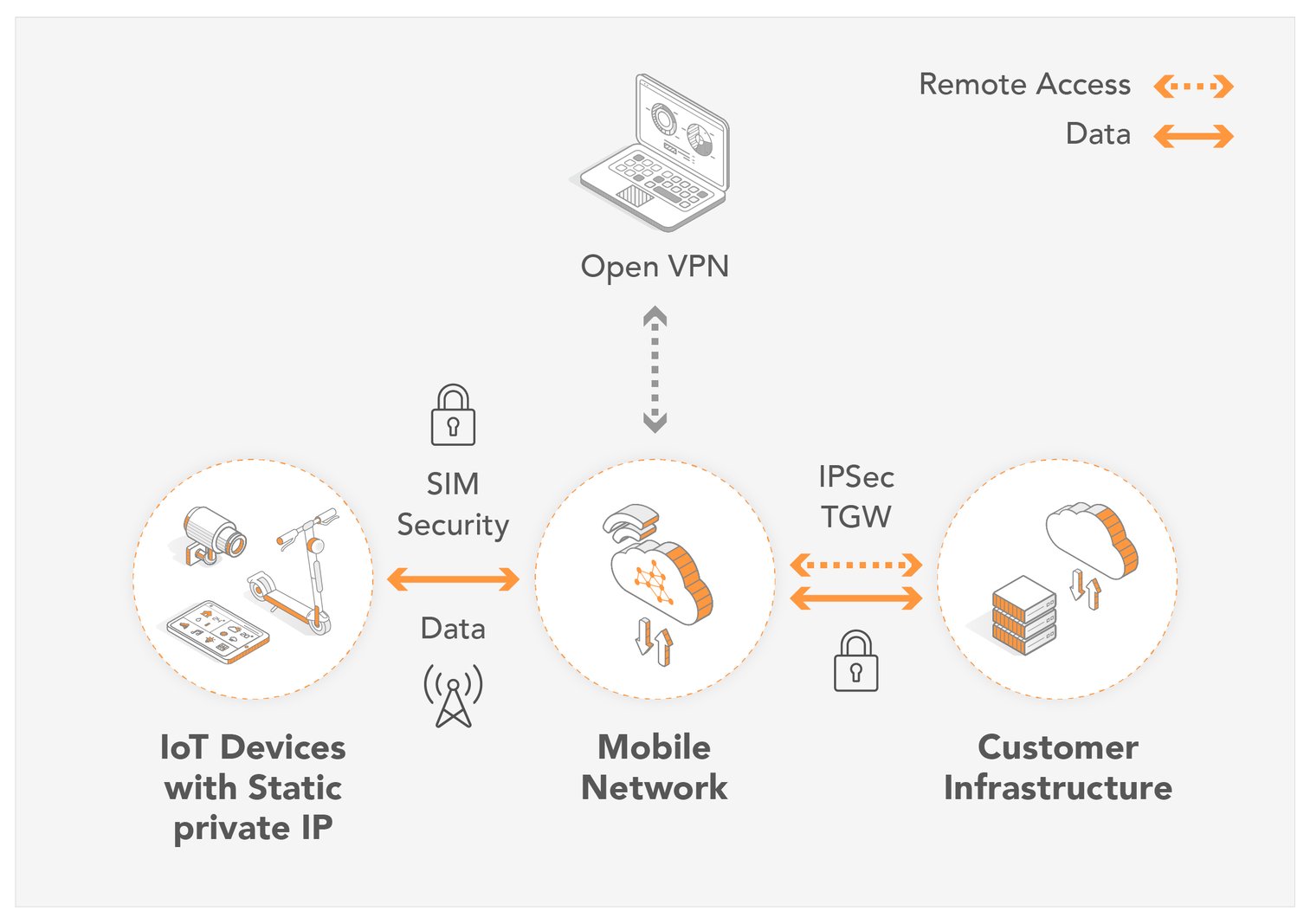
How remote device access helps IoT businesses emnify Blog